Suppose Nikita's public key is 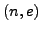 and her
decryption key is
and her
decryption key is 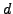 , so
, so
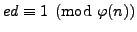 . If somehow we
compute the factorization
. If somehow we
compute the factorization 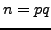 , then we can compute
, then we can compute
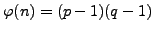 and hence compute
and hence compute 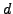 . Thus if we can factor
. Thus if we can factor 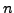 then we can break the corresponding RSA public-key cryptosystem.
then we can break the corresponding RSA public-key cryptosystem.
Subsections
William
2007-06-01